MACsec is the IEEE 802.1AE standard for authenticating and encrypting packets between two MACsec capable devices.
The Catalyst 3750-X and 3560-X switches support 802.1AE encryption with MACsec Key Agreement (MKA) on downlink ports for encryption between the switch and host devices. The switch also supports MACsec link layer switch-to-switch security by using Cisco TrustSec Network Device Admission Control (NDAC) and the Security Association Protocol (SAP) key exchange.
Cisco TrustSec MACsec for switch-to-switch security is supported only on switches running the IP base or IP services feature set.
Cisco TrustSec uses AES-128 GCM and GMAC and is compliant with the 802.1AE standard.
The follow protection levels are supported when you configure SAP pairwise master key (sap pmk)
- sap mode-list gcm-encrypt gmac no-encap : protection desirable but not mandatory.
- sap mode-list gcm-encrypt gmac : confidentiality preferred and integrity required. The protection is selected by the supplicant according to supplicant preference.
- sap mode-list gmac : integrity only.
- sap mode-list gcm-encrypt : confidentiality required.
- sap mode-list gmac gcm-encrypt : integrity required and preferred, confidentiality optional.
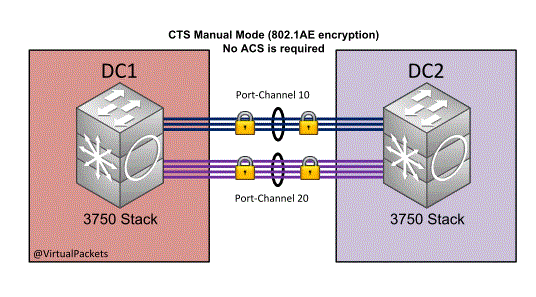
We will configure MACsec on a couple of port-channels between two data centers.
The links between the two data centers have been provided as L2 links.
Configuration:
interface Port-channel10
description *** Po10 InterDC LINKS VLANS 10,100 ***
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 10,100
switchport mode trunk
spanning-tree bpdufilter enable
!
!
interface GigabitEthernet1/0/1
description *** DC1 LINK 1 ***
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 10,100
switchport mode trunk
shutdown
udld port aggressive
cts manual
no propagate sgt
sap pmk 0000000000000000000000000000000000000000000000000000001234ABCDEF mode-list gcm-encrypt
spanning-tree bpdufilter enable
channel-group 10 mode active
!
interface GigabitEthernet1/0/2
description *** DC1 LINK 2 ***
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 10,100
switchport mode trunk
shutdown
udld port aggressive
cts manual
no propagate sgt
sap pmk 0000000000000000000000000000000000000000000000000000001234ABCDEF mode-list gcm-encrypt
spanning-tree bpdufilter enable
channel-group 10 mode active
Add the same config to the other 3750 in DC2 and we should have a encrypted link between the two data centers.
We can verify this by running the “show macsec summary” & “show macsec interface” commands.
DC1-3750#show macsec interface gi1/0/1
MACsec is enabled
Replay protect : enabled
Replay window : 0
Include SCI : yes
Cipher : GCM-AES-128
Confidentiality Offset : 0
Capabilities
Max. Rx SA : 16
Max. Tx SA : 16
Validate Frames : strict
PN threshold notification support : Yes
Ciphers supported : GCM-AES-128
Transmit Secure Channels
SCI : D40D1C4402030000
Elapsed time : 01:29:20
Current AN: 0 Previous AN: 1
SC Statistics
Auth-only (0 / 0)
Encrypt (9629197 / 0)
Receive Secure Channels
SCI : D40D1B3895910000
Elapsed time : 01:29:20
Current AN: 0 Previous AN: 1
SC Statistics
Notvalid pkts 0 Invalid pkts 0
Valid pkts 5955254 Late pkts 0
Uncheck pkts 0 Delay pkts 0
Port Statistics
Ingress untag pkts 0 Ingress notag pkts 20
Ingress badtag pkts 0 Ingress unknownSCI pkts 0
Ingress noSCI pkts 0 Unused pkts 0
Notusing pkts 0 Decrypt bytes 508339342
Ingress miss pkts 20
We are also NOT limited to the 8 VLAN limit imposed by using Trustsec enforcement as we are running MACsec.